I had to search all over the internet to figure out how to do this in ProxMox. It is much easier in esxi because you can easily create a promiscuous vSwitch and attach the VMs you wish to monitor on that vSwitch. It’s a couple clicks, and you are finished. With ProxMox, it is not quite the same story. There are quite a few things you need to consider in how you approach this. This also is not a one size all fits all solution. I will provide information about my environment that I find to be useful so you can understand why I used the approach I did. I dug through a lot of guides on the internet, none of which really specified what their environment was like (mostly true). There are some that did but weren’t clear on the hardware being used. I am going to include this, so it adds clarity.
Lab Environment
- Dell r620 Server blade
- (All VMs run on a single node)
- 4 Port Network Card (1GB Port Speed)
- eno1 – Trunk Connection to Cisco switch (Mgmt only)
- eno2 – Trunk port where all VMs are attached
- eno3 – Thinking about putting Security Tools on this interface (and not capturing on this)
- eno4 – Connected to SPAN port on CISCO switch
- Cisco 3750x 24 Port Switch
- SPAN port configured
Prerequisite Packages that you need to Install.
apt install openvswitch-switch net-tools ethtool
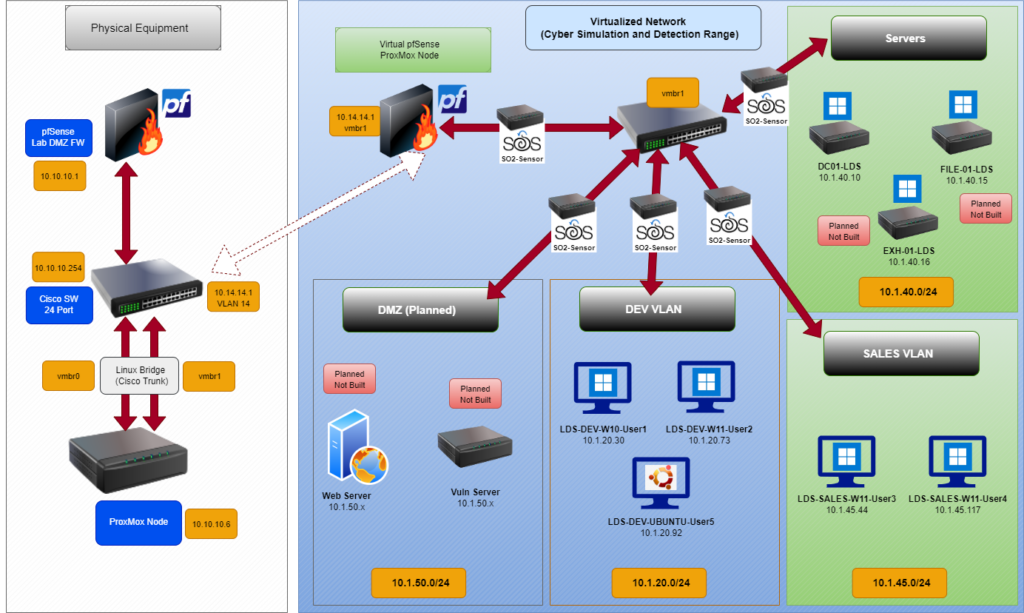
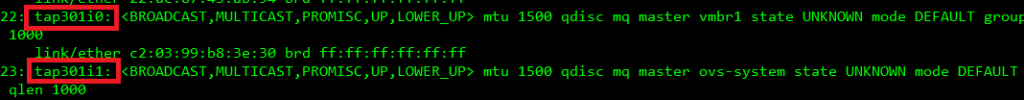
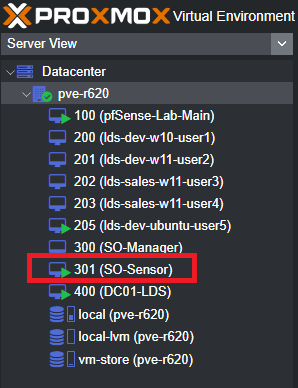
The Diagram below gives you a logical representation of what I am doing. It looks like 5 individual sensors, but it is not. I am running 1 virtual machine (sensor) with 1 promiscuous port. The diagram is a depiction of what it effectively is doing. The different VLANs are attached to the same Linux Bridge, which is essentially acting as a HUB, and I am capturing all the traffic with a SPAN session which is monitoring the physical interface of the bridge my VMs are running on and copying that to my eno4 interface which I configured ProxMox to receive on a dedicated bridge port attached to eno4 where the traffic on my switch is being copied to.
# network interface settings; autogenerated# Please do NOT modify this file directly, unless you know what# you're doing.## If you want to manage parts of the network configuration manually,# please utilize the 'source' or 'source-directory' directives to do# so.# PVE will preserve these directives, but will NOT read its network# configuration from sourced files, so do not attempt to move any of# the PVE managed interfaces into external files!
auto loiface lo inet loopback
iface eno1 inet manual
iface eno2 inet manual
iface eno3 inet manual
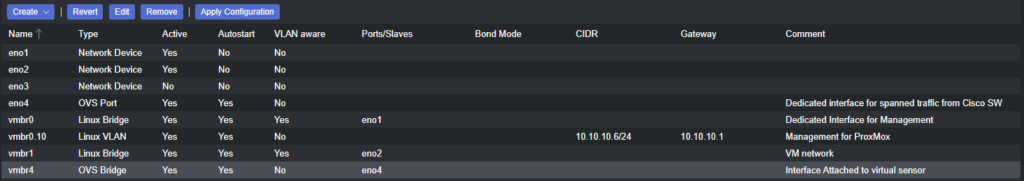
auto vmbr0iface vmbr0 inet manualbridge-ports eno1bridge-stp offbridge-fd 0bridge-vlan-aware yesbridge-vids 2-4094bridge-pvid 999#Dedicated Interface for Management
auto vmbr0.10iface vmbr0.10 inet staticaddress 10.10.10.6/24gateway 10.10.10.1#Management for ProxMox
auto vmbr1iface vmbr1 inet manualbridge-ports eno2bridge-stp offbridge-fd 0bridge-vlan-aware yesbridge-vids 2-4094bridge_ageing 0bridge-pvid 999#VM network
auto eno4iface eno4 inet manualovs_type OVSPortovs_bridge vmbr4#Dedicated interface for spanned traffic from Cisco SW
auto vmbr4iface vmbr4 inet manualovs_type OVSBridgeovs_ports eno4#Intefaced Attached to virtual sensor
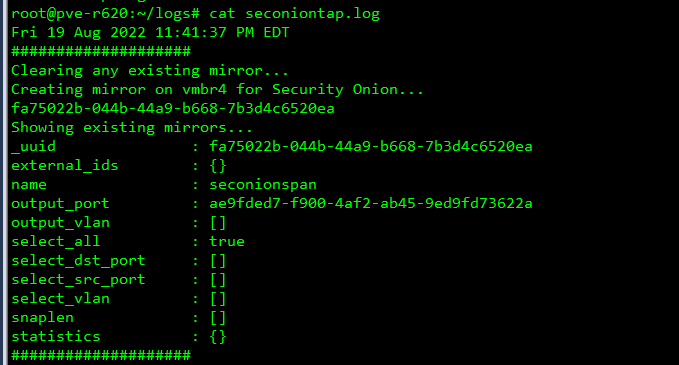
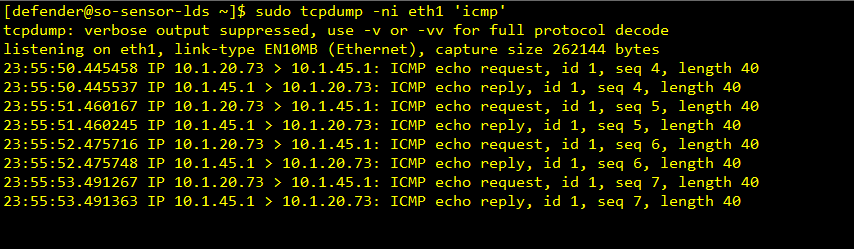
Ping Test
Capture on Security Onion Sensor