
What if I want to use esxi instead of virtual box, ProxMox, or VMWorkstation?
"Quote from HuskyHacks
Learn how to set up a truly isolated lab network for malware analysis and the safety considerations of different lab setups."
What if you have a couple of servers or unused computers that you repurposed as virtualization servers? What if you want to isolate those servers on a totally different VLAN on your home network to isolate it even more? No matter what you want to do, you have options.
Creating a host-only or isolated environment for malware testing is a crucial practice in your home office or workplace. The primary motivation behind this approach lies in the need to shield the broader network and systems from potential harm during the evaluation of malicious software.
By confining the testing environment to a host-only setup, you minimize the risk of unintended infections spreading across your network or affecting critical systems. This controlled setting allows security professionals and researchers to dissect and analyze malware without jeopardizing the integrity of the larger infrastructure. Moreover, an isolated environment provides a safe space to observe the behavior of various malware types, aiding in the development of effective countermeasures and security protocols. In essence, the choice to create a host-only or isolated environment underscores a proactive and responsible approach to understanding, combating, and ultimately defending against the ever-evolving landscape of cyber threats.
So, How do we do it?
It is much easier when dealing with a type 2 hypervisor like Virtual Box or VMWorkstation, but it is a different story with esxi. The goal is to follow a similar concept. So, what are we going to be working with and what should we familiarize ourselves with?
-vSwitch
-Port Groups
-VLANs
-Uplinks
So do not worry, these are not complicated terms to understand. Here is a picture below to convey what it is happening. Remember this depicting it logically.
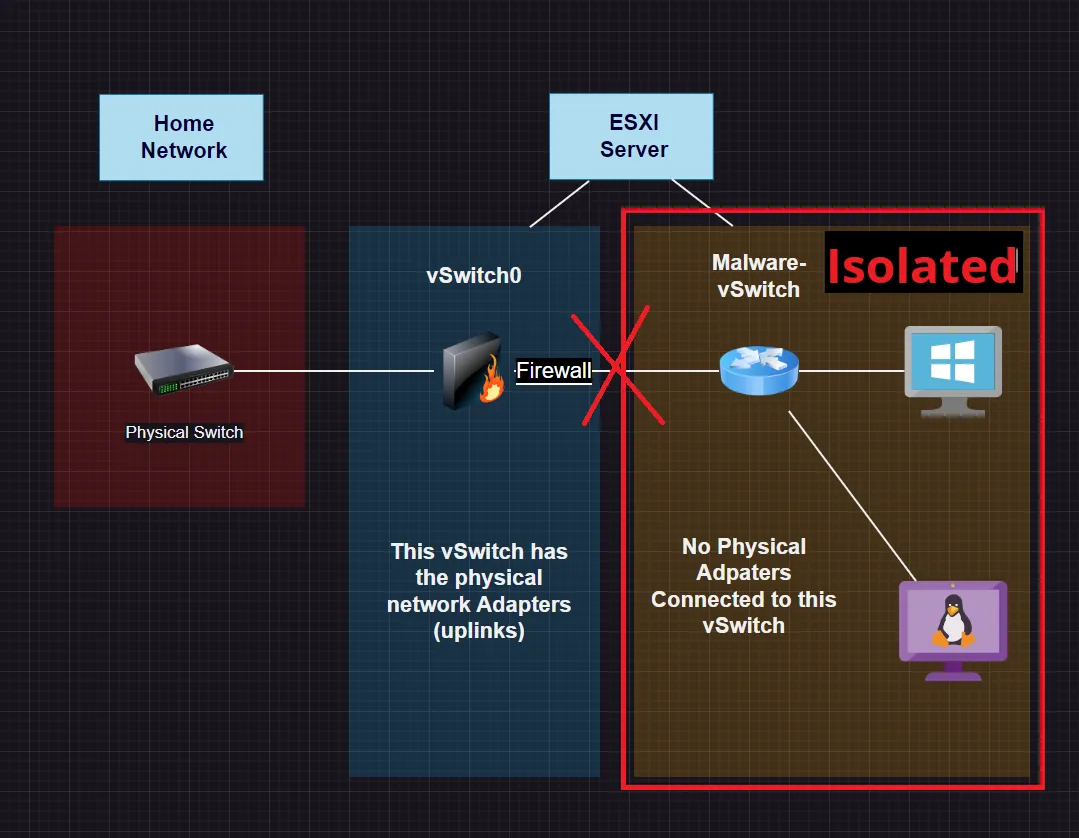
If you need internet access, you just virtually connect the router to the firewall on the vSwitch that has a connection to the physical network and out to the internet. The two vSwitches are isolated form each other and the Malware vSwitch is completely isolated in terms of having no uplink / physical network adapters connected to it.
There is a good course provided by TCM Security called, Practical Malware Analysis & Triage that covers this. What I am doing is taking the same concept and applying to VMWare esxi. While VMWorkstation and Virtual Box are type 2 hypervisors, meaning they are installed on top of an operating system, VMWare esxi is a Type 1 Hypervisor, or installed directly on hardware. That is another thing entirely, so back to the topic.
What VMs do you recommend? How do I prepare the environment?
So the great thing is, you won’t need much. This guide assumes you have already installed esxi and have working server. By default, most instances you find in the home lab will resemble the default out of the box configuration. You have a lot of flexibility to name, configure and change settings to make it more personalized and processional, but that is not really part of the scope.
By default, your everything will be attached to vSwitch0. You will find the default port group and the VMKernel. One thing to keep in mind, not everyone has the same hardware. In this situation, I have multiple Network Interface Cards (NICs) on my server, however, you only need to have 1 attached to the vSwitch for connectivity. It is best practice to have redundancy, but for the purposes of this, no need to worry about it.
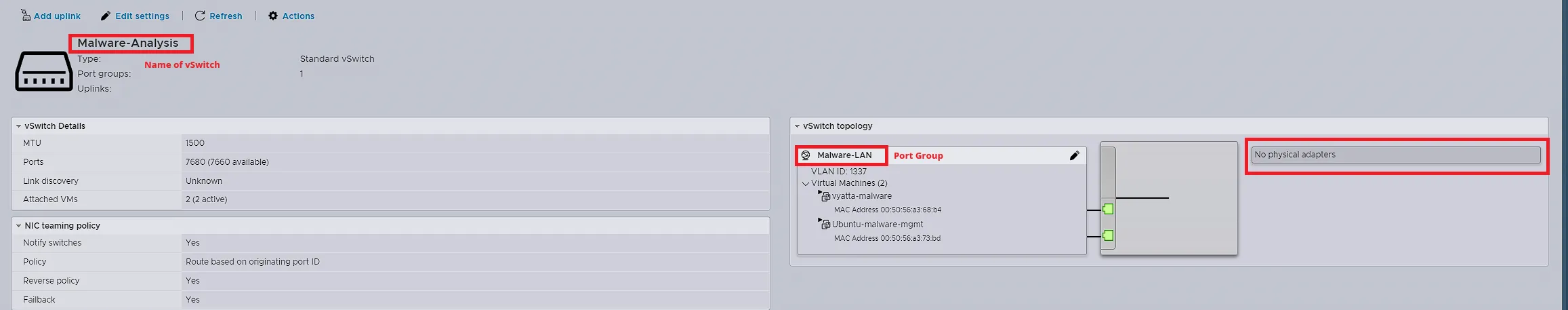
As you can see above, I created a vSwitch named Malware-Analysis, created a portgroup called Malware-LAN that is attached to this vSwitch and I have NO PHYSICAL Adapters attached. The only VM that will share a Port Group from the standard vSwitch0 is the firewall. The screenshot below is similar to the one you saw a moment ago, it’s just not showing the isolation. Instead, it will show the logical shared port-group. This is only needed for initial setup. For example, you may need access to the internet to download any tools, configurations, or the malware you wish to use to perform analysis. Once this is complete, there is no need or requirement for internet access any longer.
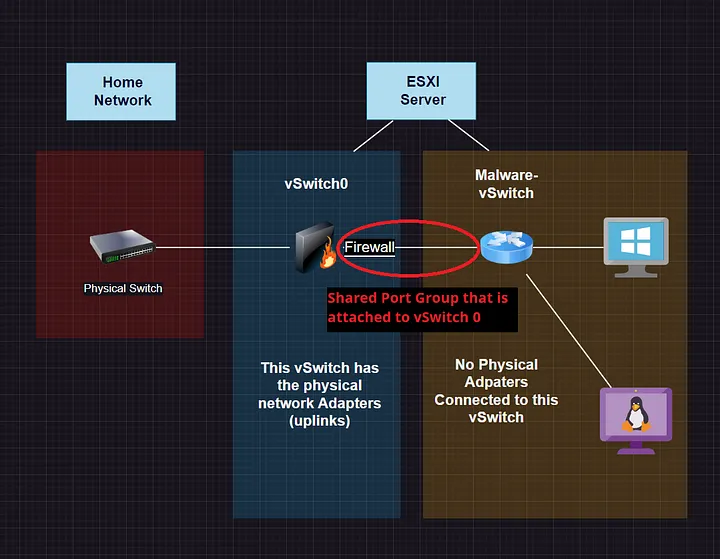
Once you download what you need, disconnect that port group all together in the vm settings. Reference the image below.
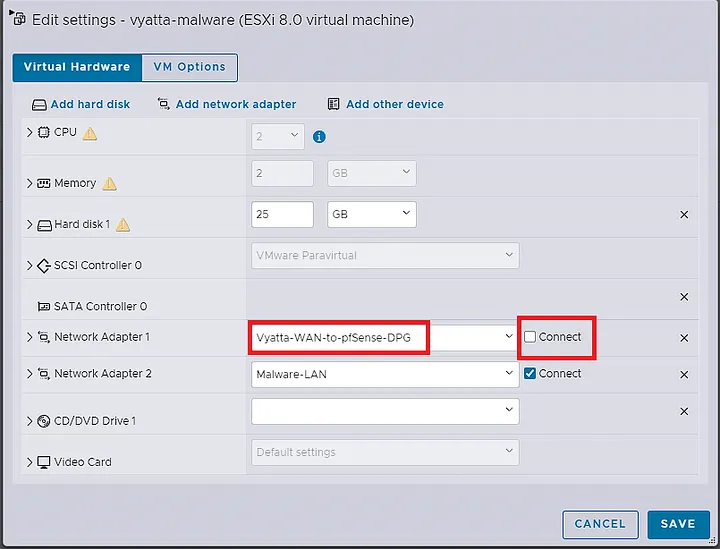
This severs any ability for the Malware vSwitch to connect out to the internet because all logical and physical connections are disconnected. There are no physical adapters on the Malware vSwitch and there is no longer any logical connection to the vSwitch that is connected to the physical network.
The Core Virtual Machines (VMs) and their purpose for preparation of the environment
The core VMs I used to make this work are pfSense Firewall and VyOS Router. The purpose that pfSense firewall is serving is the edge connection between the physical network and edge connection between both vSwitches. It gives us the ability to filter traffic and an extra layer of protection. The VyOS router serves a couple of purposes. The purpose of the VyOS router is to serve as the edge connection to pfSense to be able to access the internet if needed to download tools and make final preparations to the VMs before detonation of malware for analysis. It will also act as the DHCP server and connection for all the Malware Analysis VMs to be able to communicate with one another. After this, the pfSense firewalls serves no purpose and should not really be considered as part of the isolated environment.
The Core Virtual Machines (VMs) and their purpose in the isolated environment
The core VMs in the isolated environment will be the following Virtual Machines (VMs)
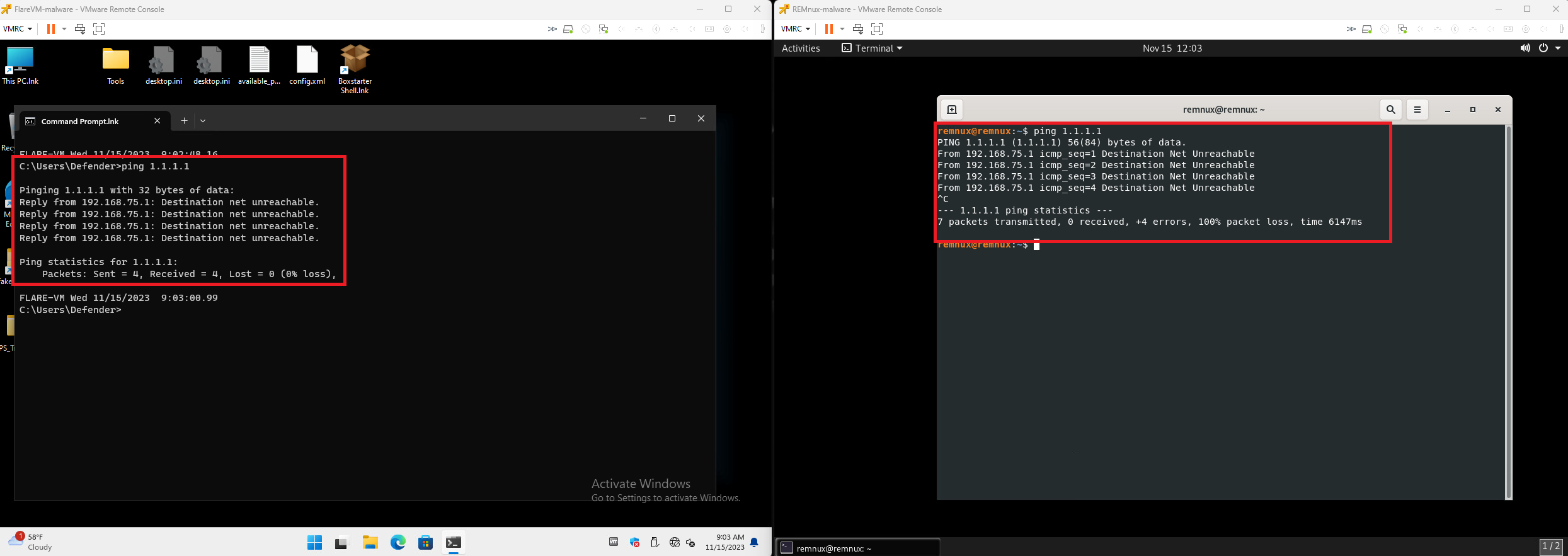
During analysis, the VyOS router will be disconnected from pfSense severing any ability for the router itself and any of the VMs to reach your home or business network, and even worse, out to the internet. Ensure you do your due dilligence and MAKE SURE THE CONNETION is disabled. We do not have the same luxury as we do in VMWorkstation or VIrtual Box as that is handled automatically for us.
Flare VM
REMNux

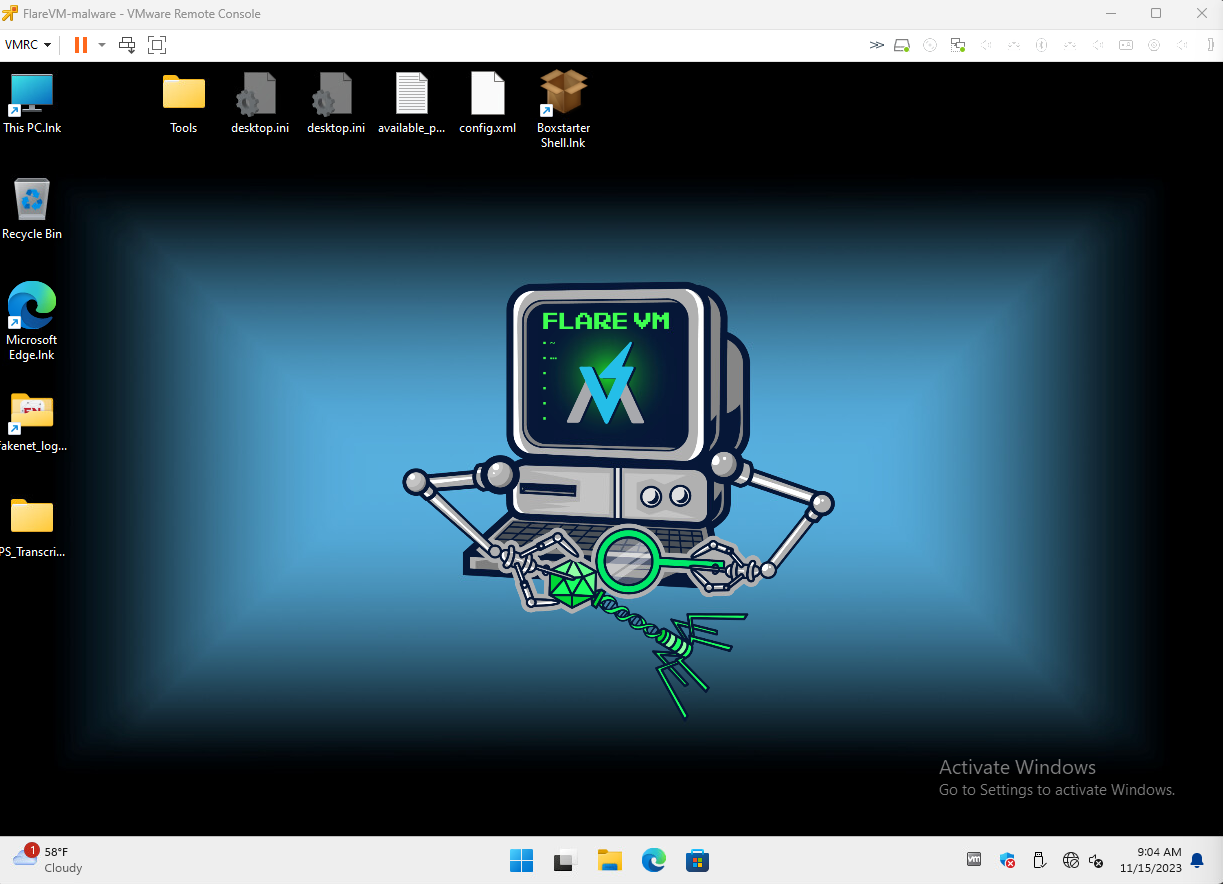
Testing connectivity to the Internet
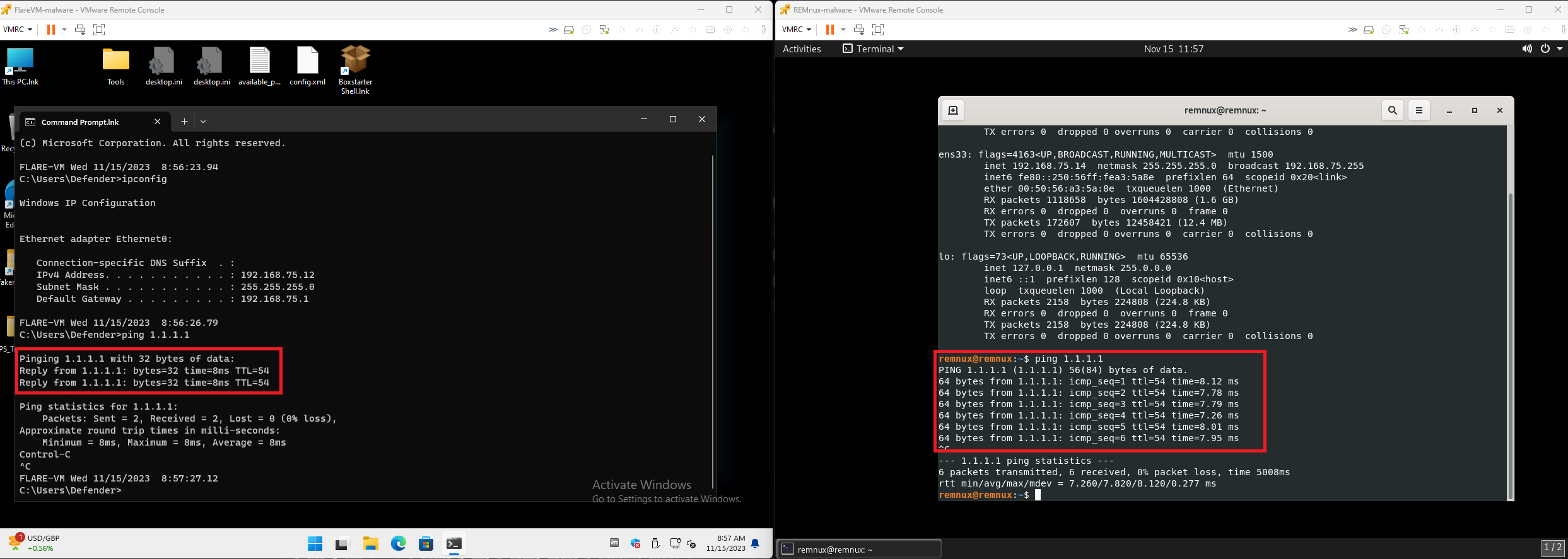
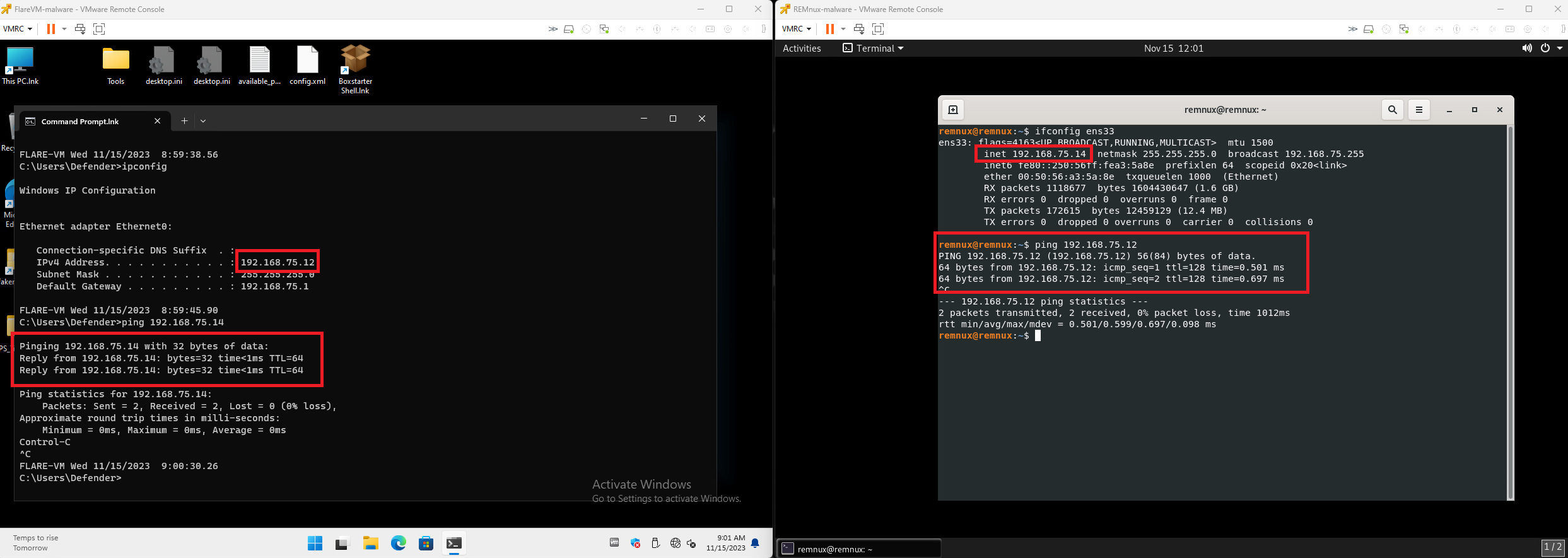
Testing Internal Connectivity between each Box
Disabled NIC on vyatta to pfSense (No Internet)
I hope this guide was helpful and happy malware testing.