- 25U Rack with Caster Wheels
- Cisco 3750x 48 Port Switch – ebay
- 24 Port Patch Panel
- VCE RJ45 CAT 6 in-line Couplers for Patch Panel – 25 Pack
- Synology NAS DS 718+
- Rasberry Pi4 – Guacamole Server
- Dell r820 Server Chassis
- Cisco UCS-C240-M3S
- Dell r620 Server Chassis
- Dell T5610 Server Tower
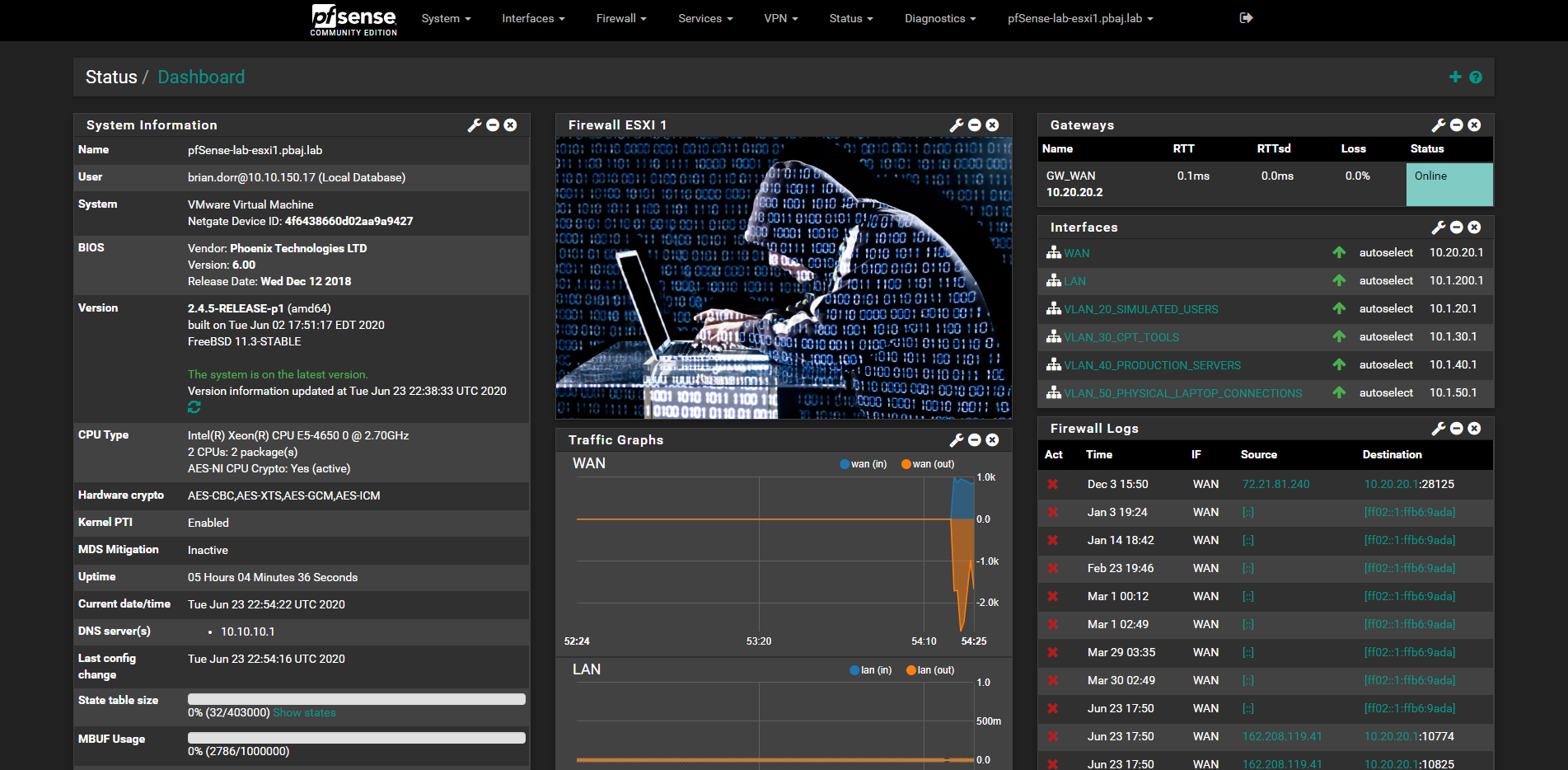
- ASUS RT 1750 (Wireless Disabled)
- HP Procurve 1810 1GB Ports (Ebay)
- HP Procurve 1800-24G 1GB Ports (Ebay)
- Domain Controllers for Lab Network (Windows Server 2016)DC1 / DC2 – DNS
- piHole DNS 1 / 2 (All traffic forwarded to piHole DNS and filtered at the main firewall) – Runs on 2x Pi 3B’s
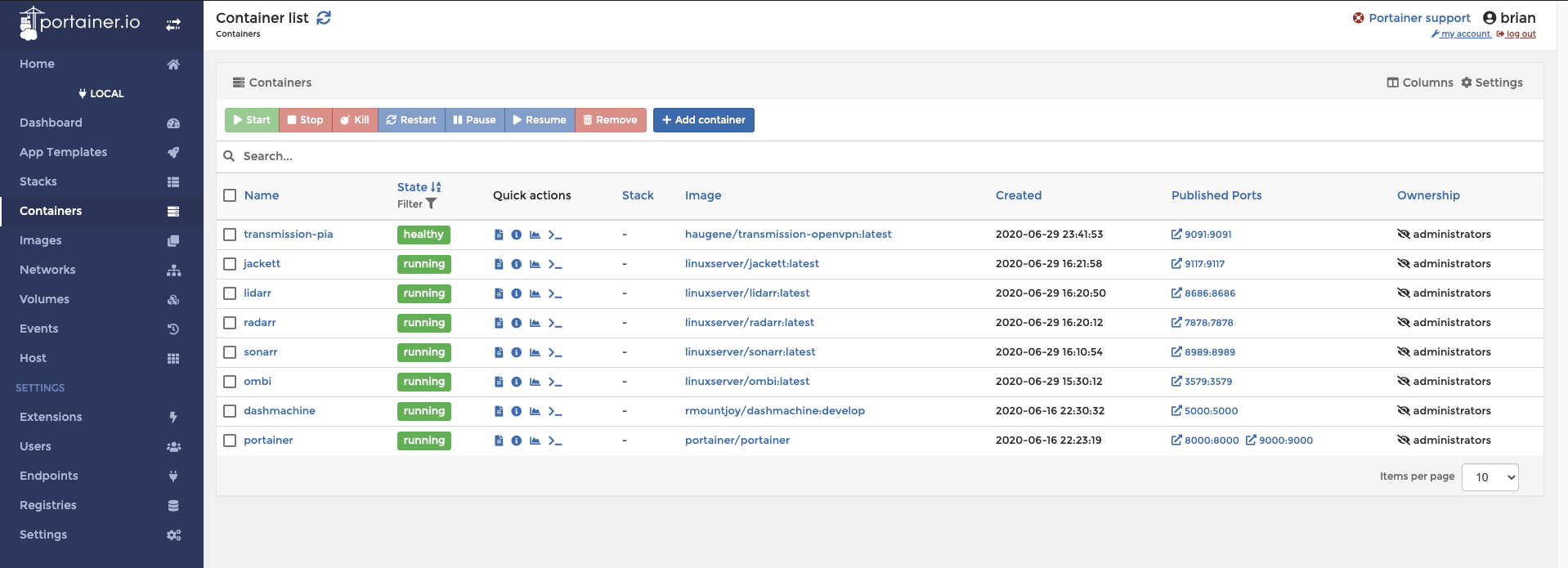
- Docker Server (Runs Portainer on a Fanless PC)
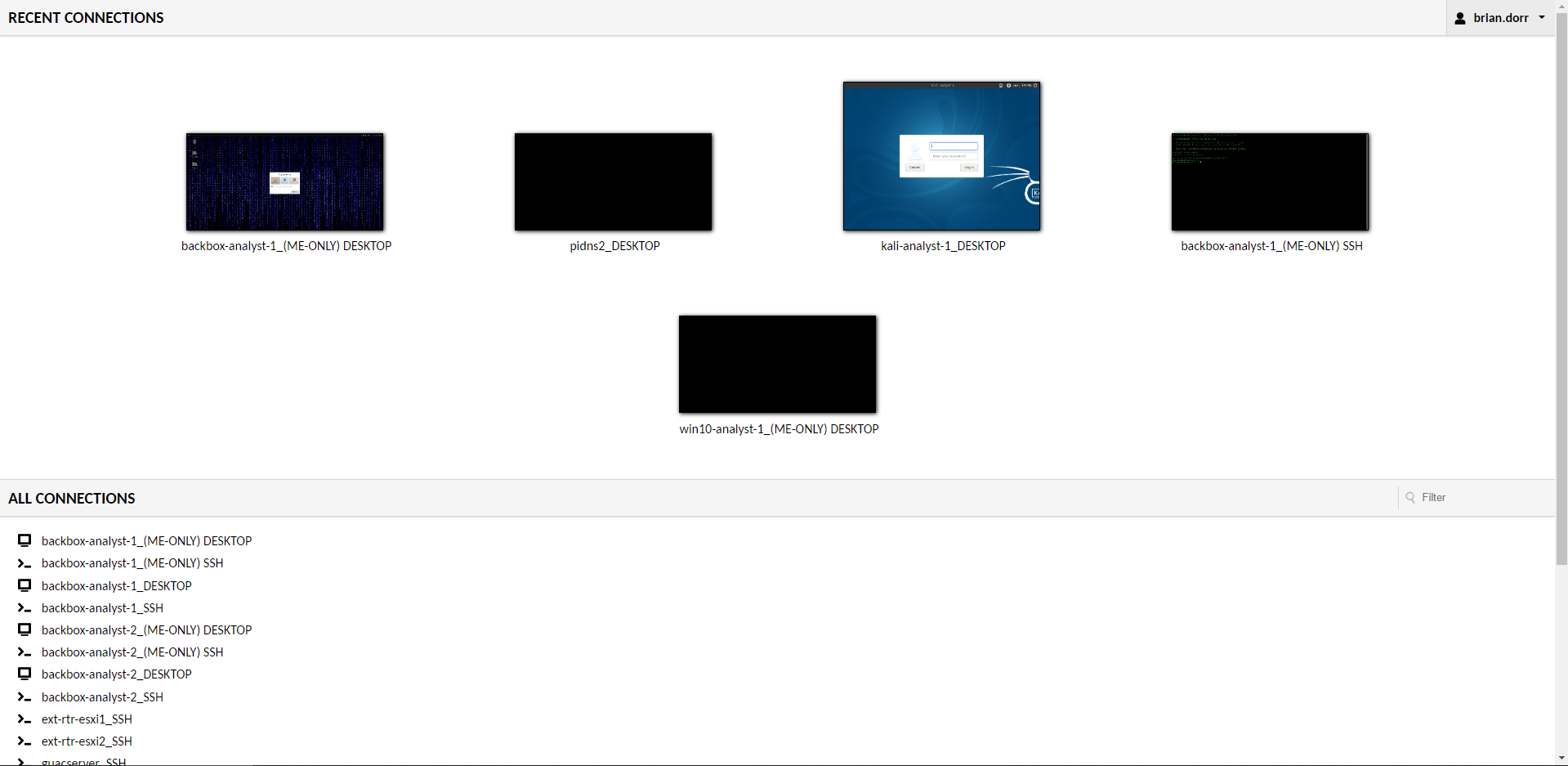
- Guacamole Server (Clientless RDP,VNC,SSH server through a webrowser) – Runs on a Pi 4
- Windows Analysts VMs
- Linux Analysts VMs
- Kali Pen Testing VMs
- Customer simulated ServicesCustomer WorkstationsWindows
- Linux
- Customer Services NetworkActive Directory (Domain)
- Exchange (Planned)
- File Services (Planned)
- Traffic Generation (Planned)
- Intrusion Detection (Planned)
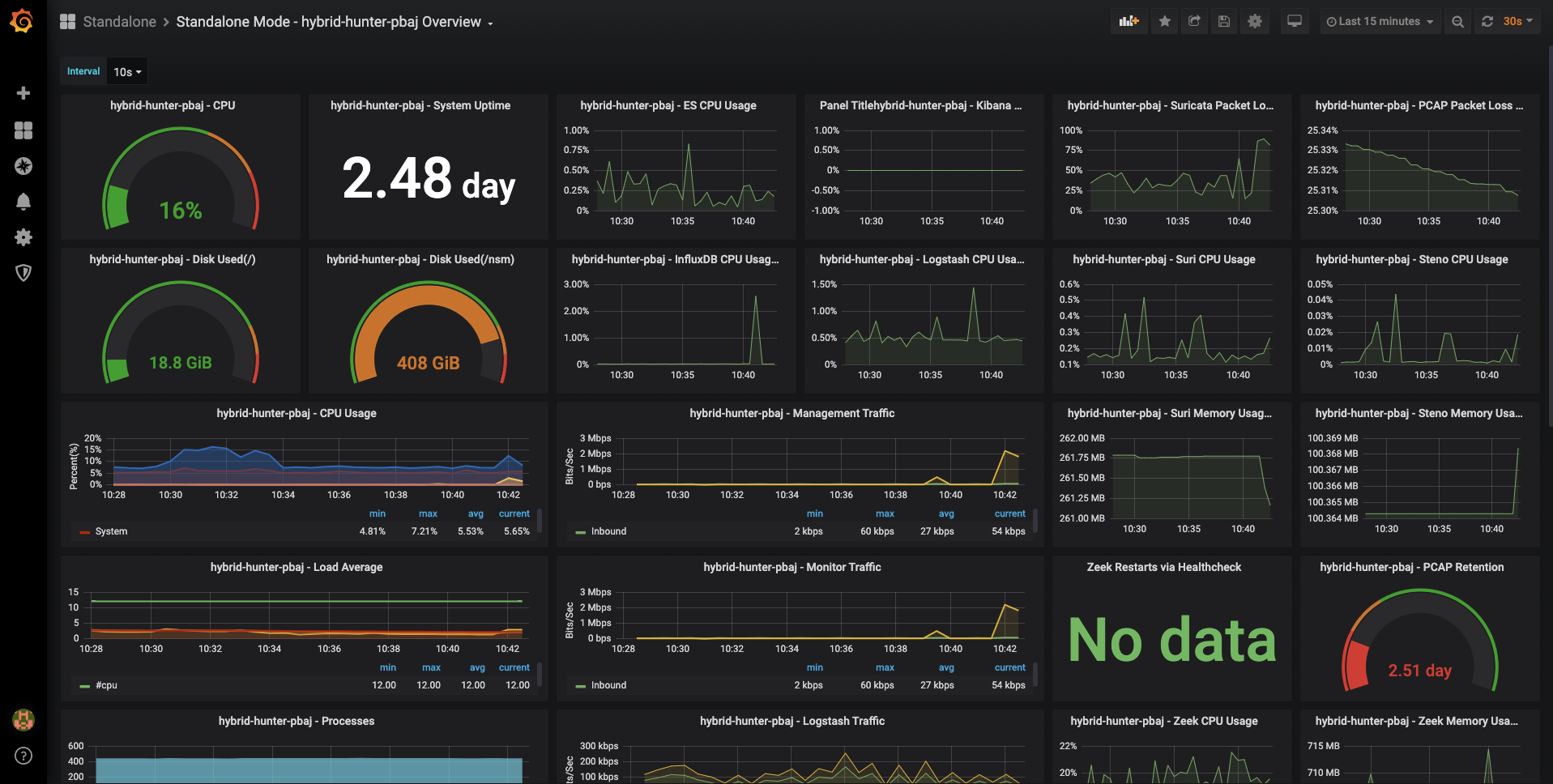
Hardware aka VM Specs
- CPUs – 16
- RAM – 32 GB
- HD – 4 TB
- 1 Virtual NIC
- 1 Virtual promiscuous Port (Connection to Mirrored port)
- Full Packet Capture
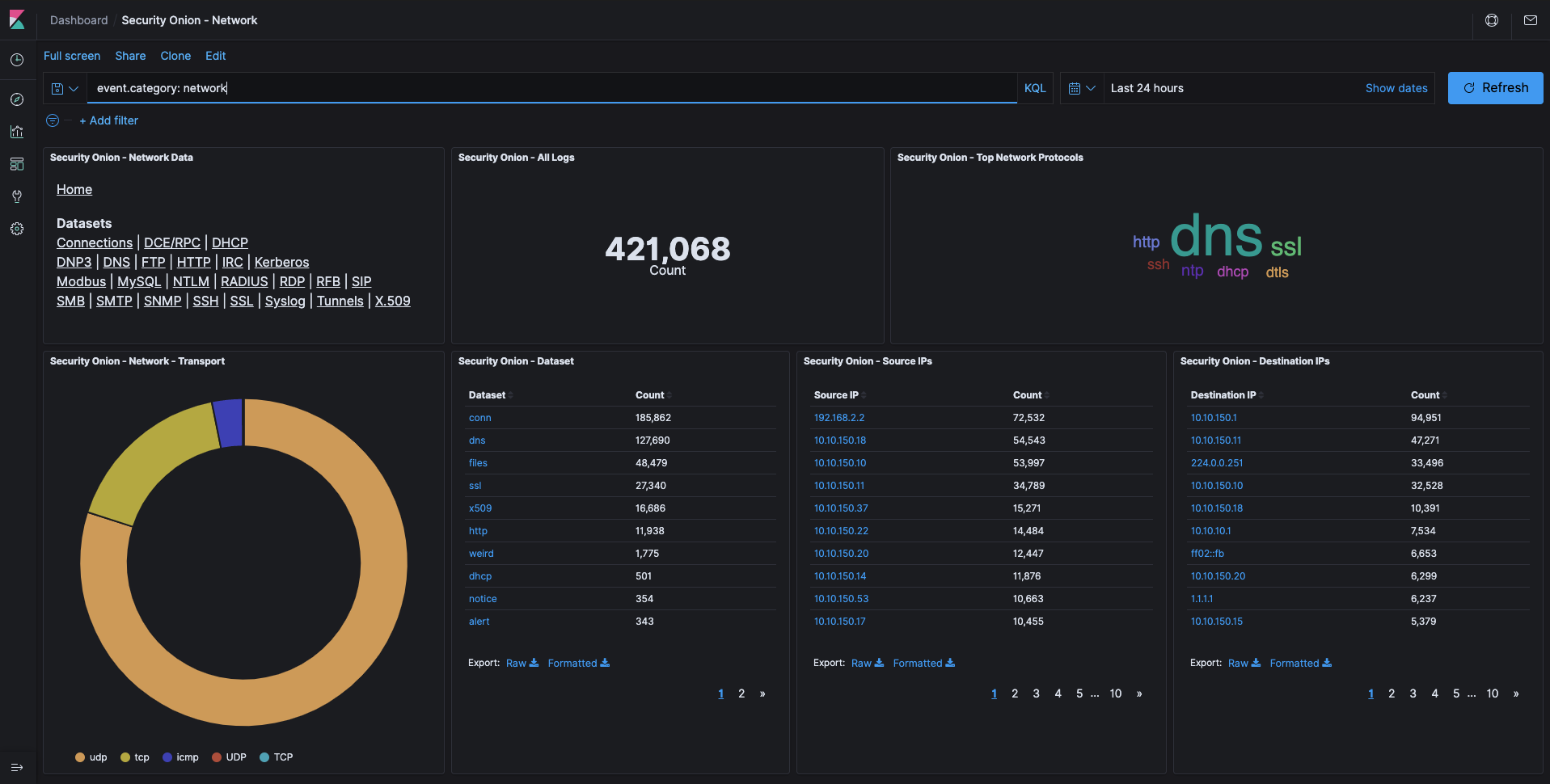
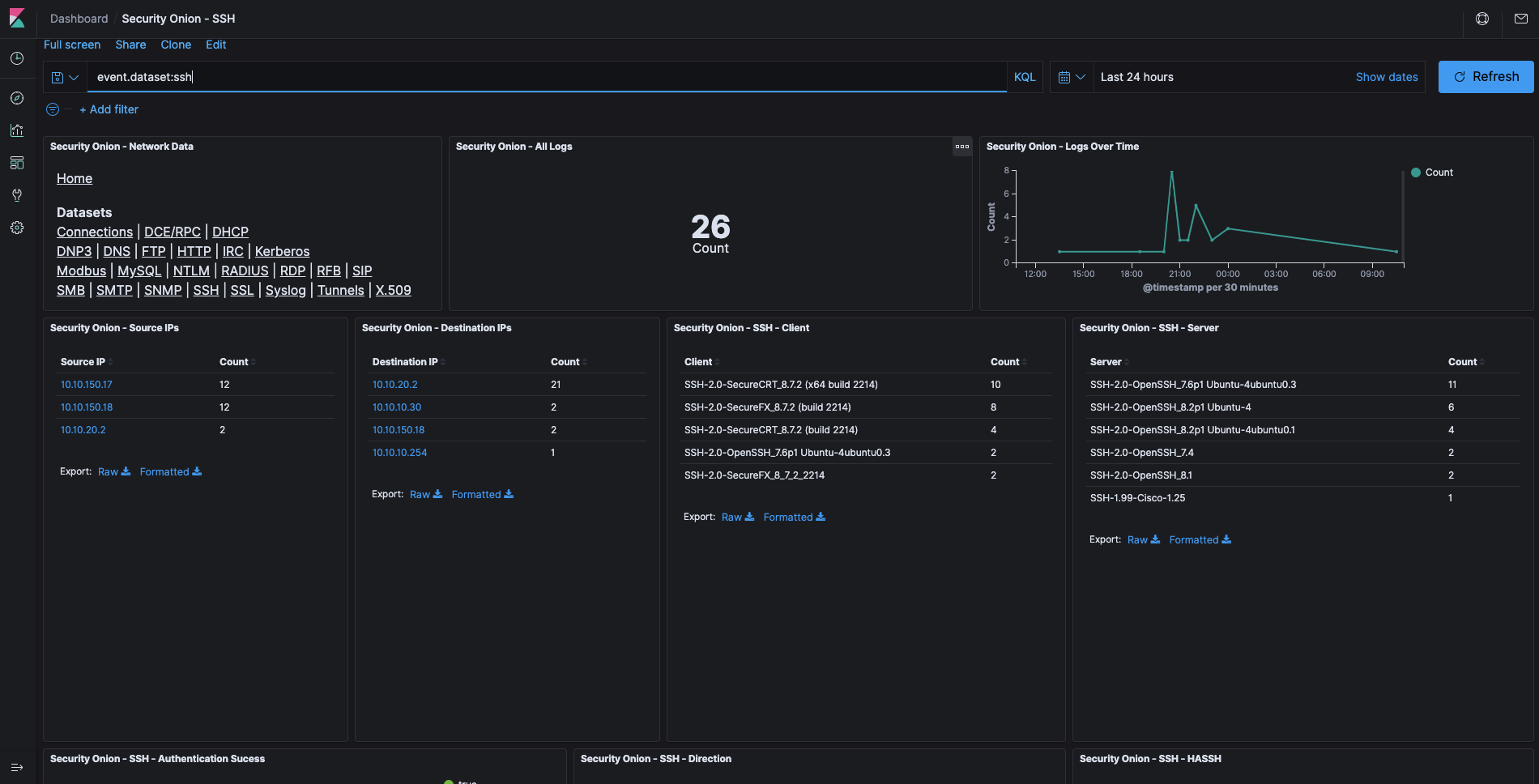
- Protocol Analysis and Metadata via Zeek.
- Signature Based Alerting via Suricata.
- Data Storage, Indexing, and Search via Elasticsearch.
- Data UI and Visualization via Kibana.
- Incident Response Platform via The Hive
- Host Security Monitoring via Wazuh and OS Query/fleet
- The Cyber Swiss Army Knife via CyberChef
- Security – The system is developed and tested to run with SELinux enabled.