Forward Proxy Configuration to pfSense
I gained the inspiration for this particular solution with talking to a buddy of mine, and we always bounce ideas off each other. He was the test dummy in this situation. You can find his post over on his site digitalmetaverse that will cover this same HA proxy solution.
Requirements
- You have completed part 1 from this post on Setting up Wireguard
- You updated pfSense to version 2.5
You can process if you have completed the requirements
HA Proxy Setup and Configuration Below
Below are the commands to get haproxy configured on the frontend (VPS) and forward downstream through the tunnel.
sudo apt install haproxy -y
sudo nano /etc/haproxy/haproxy.cfgNext, paste the following into the config file (Over-write everything in there):
global
log /dev/log local0
log /dev/log local1 notice
chroot /var/lib/haproxy
stats socket /run/haproxy/admin.sock mode 660 level admin expose-fd listeners
stats timeout 30s
user haproxy
group haproxy
daemon
# Default SSL material locations
ca-base /etc/ssl/certs
crt-base /etc/ssl/private
# See: https://ssl-config.mozilla.org/#server=haproxy&server-version=2.0.3&config=intermediate
ssl-default-bind-ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384
ssl-default-bind-ciphersuites TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256
ssl-default-bind-options ssl-min-ver TLSv1.2 no-tls-tickets
defaults
log global
mode tcp
option tcplog
option dontlognull
timeout connect 5000
timeout client 50000
timeout server 50000
errorfile 400 /etc/haproxy/errors/400.http
errorfile 403 /etc/haproxy/errors/403.http
errorfile 408 /etc/haproxy/errors/408.http
errorfile 500 /etc/haproxy/errors/500.http
errorfile 502 /etc/haproxy/errors/502.http
errorfile 503 /etc/haproxy/errors/503.http
errorfile 504 /etc/haproxy/errors/504.httpfrontend https
bind *:443
option tcplog
mode tcp
default_backend httpsbfrontend http
bind *:80
mode http
option httpclose
default_backend httpbbackend httpsb
mode tcp
server main 192.168.4.2:443 send-proxybackend httpb
mode http
server main 192.168.4.2:80save and exit.
Run the following commands to check the configuration (should be good) and restart the service:
haproxy -f /etc/haproxy/haproxy.cfg -c
sudo systemctl restart haproxy.serviceReverse Wireguard Side
I wont be going over this, as Lawrence Systems on YouTube does an amazing job detailing this process (per usual).
Reverse HAproxy side (pfSense)
Now we move to the “backend” haproxy to configure this…one…option….or you will be troubleshooting for ours. In frontend, click edit on your https frontend and enter accept-proxy in advanced options.
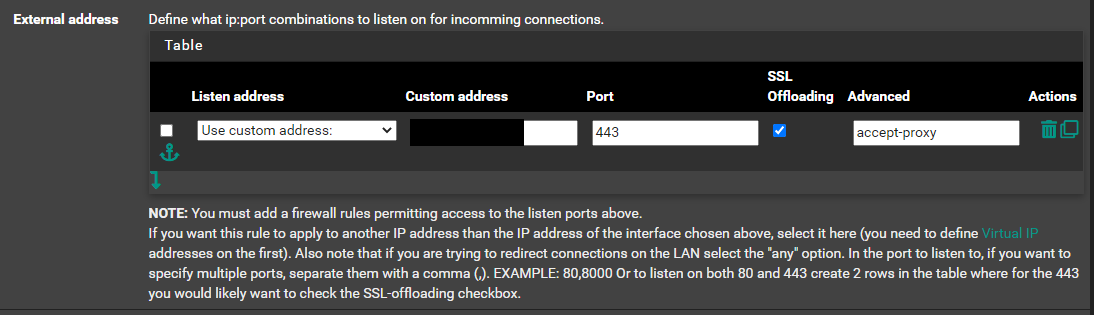
Make sure to set the listening address to “Custom” and as the IP of the vpn as you see in the picture above. (This the pfSense Internal Side of the Wireguard tunnel network you chose).
AND THAT’S IT!
If you need information on how to setup HA Proxy on pfSense for SSL offloading this will be pretty benefical.