Packet Analysis and Why
Packet analysis is very important in discovering the events that have lead to a compromise, or even just troubleshooting. It is probably good to question the first thing that comes to mind when someone says packet analysis to discover the lens you are reading this post in. There are many utilities for conducting packet analysis. and it is not just for finding evil. Why am I saying all that? Because you need to have an objective or a goal for doing it right? Yes, that is correct. It would be silly to just start grabbing pcap files and just opening them up in Wireshark with no objective or goal in mind. This post is going to focus more on a methodology and is based around finding evil. To look for evil does not mean we will always find evil. The focus is the methodology that will help us do that over time.
So why tshark?
Good question to ask, what can tshark do that wireshark can’t or any other packet analyzer for that matter. It is much easier when you are trying to dive deeper into a packet with tshark than wireshark. I like to use wireshark initially just because of the profiles you can use to make your searches a bit more standardized, but when it comes to trying to get a more specific answer, the ability on the command line to sort and manipulate the data gives you a bit more flexibility.
tshark Fields to analyze PCAPs
You are going to want to get to know these types of options to help you narrow down the data you are looking for. There a lots of fields you can look at, however, you will want to develop some sort of methodology so it is not just taking wild stabs at a pcap in the dark
Fields (few examples)
ip.srcip.dstip.protoudp.dstportdns.queryhttp.user_agenthttp.request.methodhttp.request.urihttp.request.full_uri
I wrote a blog post about this on my medium page that has more about this, but I am now going to transition into magic shark and the reason why I developed it the way I did. It still needs some work, but its a good starting point.
Time to Introduce Magic Shark
There are several ways to do analysis on captured network traffic. Many are familiar with Wireshark, and with that being said, those of us who use it understand it is not great with very large pcap files. So why use tshark when you have a very user-friendly graphical user interface in Wireshark? Simply put, the command line always offers more flexibility and efficiency. It is easier to rank, sort and manipulate the data to only show what you want to see versus being shown everything by default and spending hours creating filters and views to get Wireshark to show only what you want. The ability to utilize multiple command line utilities like sort, awk, grep and so on is priceless. Graphical user interfaces are often limited to that where the command line is usually limited by your imagination. Lastly, your profile doesn't always follow you from device to device. Imagine having to rebuild all those search filters from scratch. You do not have to worry about that with Magic Shark, that is why it is magic!!
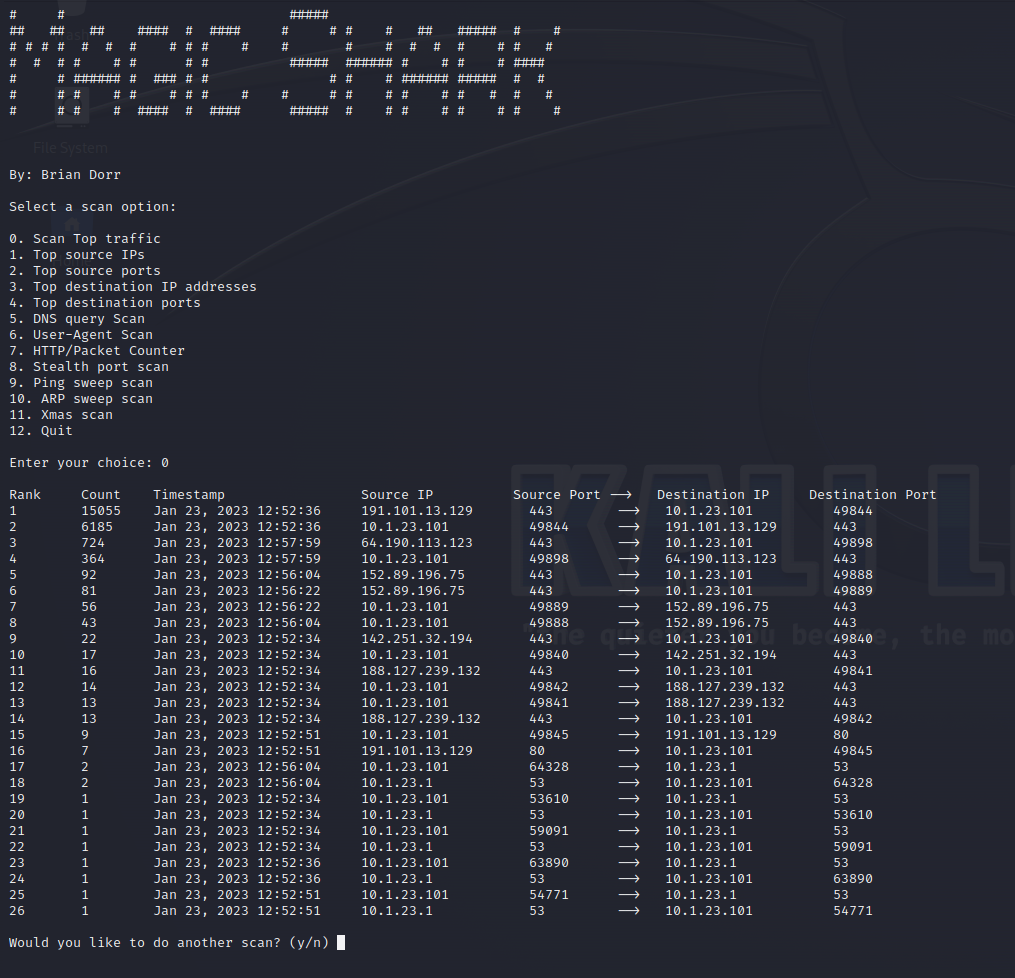
Before we get into how it works and what it is, I want to cover the intent behind this tool. I wanted to create quick search queries that have some meaning behind them. What I mean is we don't just scroll through a packet capture aimlessly. This is something you come to understand after doing analysis ovet the years. You begin to learn what things are normal, and what appears to be anomalous. As a security professional, you will become very intimate with the terrain you defend, and with that comes the knowledge of what is supposed to be there, and what isn't. While there are many uses for packet captures, one being troubleshooting, that is not our focus or goal. Our goal is to identify the top traffic, top source IPs, Top ports, and User agents for example. This will give us a quick view of the network and see if any further investigation needs to be done. For example, depending on policy, your organization may not allow itunes or spotify to be used. With magic shark, I can quickly conduct a scan on what user agents are out there and have it ranked from highest to lowest in terms of how many times it was observed.
The limit on what can be done is to the limit of a person's imagination.
How do I get it?
Magic shark is a tool written in python that allows you to analyze pcaps. There is no functionality built in for live capture. This is only meant for analysis on already captured pcaps. There are 12 hunts you can select from currently. There may be more added in the future. You can find it on github here
Review the readme for instructions on how to utilize it and to view some of the screenshots. I welcome suggestions on how to make it better, but, I can't promise the time I will have to maintain it.